by Steve Cunningham
This month we’re going to examine an issue that has nothing to do with recording, editing, or processing audio. However, it has everything to do with radio professionals, production professionals and pro voice actors, because all these use websites and email as an integral part of getting their respective jobs done. We all have multiple email accounts and visit hundreds of websites as part of our daily routines, and often share critical personal and business information via those channels. Yet we hear stories monthly (and often weekly) about accounts being hacked and personal information ending up in the hands of various nefarious characters and even criminal enterprises.
Yet there is one aspect of our use of electronic data communication that we can easily fortify against those who would steal that information, yet few of us actually do it. It’s simple to implement, costs virtually nothing, and makes our precious information much more difficult to utilize for malicious purposes. That aspect is our method of authentication and choice of passwords. And yes, the title does refer to the Marx Brothers’ 1932 classic “Horse Feathers” and no, the password should definitely not be swordfish. Why not, and what’s the harm anyway? Let me tell you a little story.
LOUIS VITTON! CHEAP!
One of my web clients has a website that we run on a secure and fast server for performance, and uses an online anti-malware monitoring service for security. The site includes a News Page where she can post informational articles and images, with a Comment feature so that visitors who register on the site can respond to her postings. A spam filter evaluates each comment for the presence of tell-tale links to “spammy” websites, and removes the comment if such links exist. Comments that pass muster are automatically routed to a holding area, where they remain until my client responds to an automated email request to approve the new comment for posting on the page. The email contains a preview of the content so she can decide whether to act on the request or not.
Just before Thanksgiving, she complained about receiving a large number of emails from the site, with comments for approval that contained “spammy” links to a site selling counterfeit designer handbags. On investigation I discovered that over 900 spammy comments had collected in the holding area over the past three days, bringing her site to a crawl in the process. After deleting the comments, I further discovered that the spam filter had been disabled. Worse yet, another spam comment appeared about then, and it was then that I remembered the “admin” user’s credentials she’d given me to get into the back of the site.
The admin password was 8tinkerbell8. That’s a very weak password, so I changed it, restarted the site, and re-logged in. The spammy comments stopped coming.
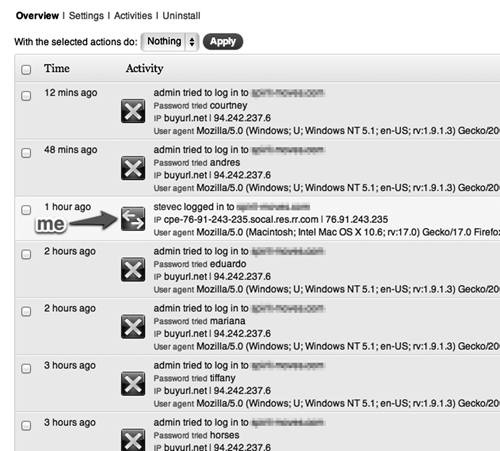
An analysis tool revealed what was happening on the login page, some of which is shown below. If you look closely you can see that the attacker, likely a software “robot” program, is trying to guess the admin user’s password in what is known in the trade as a “dictionary attack” to gain the ability to control the site, and in particular to defeat the spam filter. Such a dictionary can easily be found online, and it works because, according to Wikipedia, “...many people have a tendency to choose passwords which are short (7 characters or fewer), single words found in dictionaries, or simple, easily predicted variations on words, such as appending a digit. However these are easy to defeat.”
In other words, even though her online business is located in a good neighborhood with a good security service monitoring the property, her weak password essentially left a side door unlocked for a spammer to find. Similar attacks are equally effective in hijacking one’s email account, or even one’s bank account.
Equally troublesome is the fact that many people use the same password on multiple websites and accounts, and link those accounts to each other for the sake of convenience. Just ask Mat Honen, whose Google account was taken over then deleted, whose Twitter account was used to broadcast nasty messages, and whose AppleID account was hijacked by hackers who used it to remotely erase his iPhone, iPad, and MacBook. The sad story is here: www.wired.com/gadgetlab/2012/08/apple-amazon-mat-honan-hacking.
HOW ABOUT A NICE GAME OF CHESS?
Computer hacking has been with us for a long time, and there’s no reason to re-hash that story here. Suffice it to say that hackers, like the poor, will always be with us. What has made a difference in the past few years is the amazing performance increase in computers and processors, and thus their ability to literally guess passwords in very short order. In fact, today’s potential hijackers create machines that consist of powerful GPUs (graphic processing units (essentially video chips), which are even faster at the type of repetitive operations involved in these attacks.
At a November conference called Passwords^12 in Oslo, Norway, one of the presenters showed off a “rig” that uses multiple computers, each with 25 AMD graphics chips, to crack passwords that are actually encoded (hashed) to render them unreadable. He set up a demonstration in which the rig was able to crack any Windows XP password within six minutes. Granted, Windows XP passwords max out at 14 characters and use an outdated form of encryption, and his so-called rig is a highly-specialized, powerful machine that needs direct access to the computer being hacked. Still, more than anything it demonstrates the power that bad guys can muster if they’ve a mind to do so. It’s a bit like saying “if someone wants to steal my car, they’ll find a way to steal my car.” But that doesn’t mean that we don’t lock our car doors.
However, there are a simple set of guidelines for passwords -- what the hey, let’s call ‘em rules -- that can diminish the chances that we’ll be victimized in some way by a cyber criminal. Let’s lay them out, then I’ll explain ‘em.
SIX SIMPLE RULES
1. Use a password vault program to memorize complex passwords.
2. Use a long, complex password with upper- and lowercase letters, numbers, and symbols.
3. Don’t reuse a password on more than one account.
4. Connect to websites via https, rather than http, whenever possible.
5. Use two-factor authentication on accounts wherever possible.
6. Don’t use a mobile phone for banking. Just. Don’t. Trust me.
CREATING AND STORING PASSWORDS
Rule number one is simple, so I’ve listed it first. It will also make more sense as we consider the implications of the remaining rules. But for even simple passwords, a password management program, or vault, will make life a lot smoother. There are several available out there, and the best meet certain criteria. First, they’re available for all desktop and mobile platforms; second, they store passwords in an encrypted format that can’t be read by any person or program that doesn’t have a master password; third, they’re simple enough to use that they will actually be used, and will automatically bring up the correct password for any given website or email account.
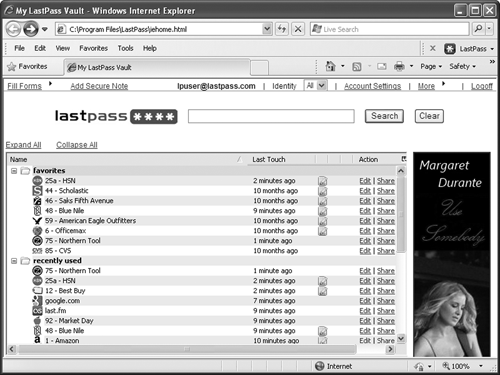
There are two I know that meet these criteria. One is web-based lastpass <www.lastpass.com> which works on just about every platform, and because it’s web-based it is available all the time. There is a free version that doesn’t support mobile phones, but for a subscription at a dollar a month, the Pro version supports everything. When installed, the lastpass icon will appear in every app that needs a password, and logins are a one- or two-click operation. The other is 1Password <www.1password.com> which works on Windows, Mac, iPhone, and Android. 1Password is an application that stores passwords in an encrypted form on the device where the program lives. It supports Dropbox, and passwords stored on Dropbox are both encrypted and available on any Dropbox-enabled device. 1Password costs $70 USD, but it’s a one-time charge and they run discount deals regularly. I’m a happy 1Password user.
Rule number two is to use complex passwords. The good news is both vault programs above include password generators that take the work out of creating really strong passwords. There are also online generators, including a good one at Gibson Research Corp <www.grc.com/passwords.htm> and many others. Random is good, as are symbols, and research has shown that length is perhaps more important than complexity. Remember, password guesses that are incorrect don’t show the guesser which characters are correct, as seen in the movie “War Games”. If the guess is wrong, then it’s all wrong and no useful information can be gleaned from the attempt, which explains why longer is harder to guess.
Unfortunately some sites do not allow long passwords, or the use of symbols. At the university where I ply my trade, the max length for a password is eight characters, and many symbols are not allowed. I do the best I can with that by using as random a string as a generator can generate.
Rule number three, don’t reuse passwords, is more than adequately illustrated in the Wired article on Mat Honen referenced above. But if that’s not enough, consider that the recent theft of 6.5 million usernames and passwords from LinkedIn affected over 2 million eHarmony.com users, who used the same credentials on both sites. You are storing all your different passwords in a vault program, aren’t you?
HTTPS, TWO FACTOR AND BANKING
Rule number four admonishes us to connect to the Interwebz using encrypted Secure HTTP, or HTTPS, whenever possible. Most large sites -- Facebook, Twitter, Amazon, and Paypal -- have already switched to https today by default. Others have not yet, but the Electronic Frontier Foundation has an add-on for Firefox (with Chrome coming) that will attempt to be secure at all times, called Https Everywhere <www.eff.org/https-everywhere>. Just check the URL bar of your browser, and look for the green lock logo or for https:// at the front of that address, particularly at your bank’s website.
Number five suggests that two-factor authentication is the greatest thing since sliced bread. When you log in under two-factor, you must present two forms of identification -- one you know (your password) and one you physically have (typically a number that arrives on your phone via SMS or via an app). While it is a minor inconvenience, it is highly secure. The most notable services that make two-factor available are Google and Paypal, and each must be set up to use two-factor authentication. Google has a great post that explains the process in detail at <googleblog.blogspot.com/2011/02/advanced-sign-in-security-for-your.html> and has links to take you to your security settings where you can enable two-factor. Google also has an app called Google Authenticator for both Android and iOS which generates the codes in real time on your phone, and has been judged most convenient by the paranoid amongst us (yes, that would be me).
Paypal’s two-factor authentication has but one potentially large drawback -- the screen where you enter the code from SMS has a button for those who “Don’t have your phone?” which appears to completely defeat the entire process. Nevertheless, it is better than nothing.
Finally, rule number six implores you against performing online banking using your cell phone. The fact is that most phones do not transmit adequately-encrypted data; some, like the Android, have no encryption at all out of the box. Yes, it is possible to add encryption on a phone via third-party apps, but the fact is that the 3G radio signal -- which is carrying your banking data through the air -- uses an encryption scheme developed in the late 1990s, and which is easily cracked today. The encryption scheme for 4G connections is more secure, but the entire thing makes me nuts. In my opinion, the Chase commercials where people send photos of checks from their phone to the bank as a deposit is about the most brain-dead scheme ever, and will continue to encourage me to keep my finances somewhere other than Chase, where convenience evidently trumps security. Your Mileage May Vary, but that’s how I roll on that subject. Bank from a laptop where you have an encrypted connection over a (hopefully) private, password secured Wi-Fi connection, but not from Starbucks. Or from your phone.
Practicing safe password may throw you off for a week or so, as you learn to love your password vault and incomprehensible passwords. However, you will sleep a little better at night than do those LinkedIn-eHarmony members, I can tell you that.
♦

