by Steve Cunningham
By now everyone who uses a computer online is aware that a certain US-based three-letter government agency is busily vacuuming up vast quantities of Interwebz traffic into its servers, storing that traffic for later use in its various intelligence operations. For better or for worse, depending upon your political proclivities, thus far few seem terribly concerned about this potential loss of personal privacy, save for the governments of other countries who are concerned about their own security, and a small group of online privacy advocates including the Electronic Frontier Foundation <http://eff.org>.
This month I would like to bring to your attention on online privacy and security matter about which I believe everyone can be concerned. It involves a piece of computer malware which raised its ugly head during the first week of October, 2013. Its sole purpose in life is to hold all of the files on your Windows-based computer hostage, and threatens to kill them all if you, the computer user, don’t pay up. Users running Windows 7, Vista, and XP are all vulnerable.
CRYPTOLOCKER RANSOMWARE
This latest bit of nastiness that has emerged from the bowels of the Interwebz is a malicious Trojan virus known as CryptoLocker. The term Trojan refers to the (possibly) mythical tale of the Trojan horse, in which a magnificent statue of a horse, full of armed Greek soldiers, was accepted by the residents of the Roman city of Troy as a gift. Once inside the walled city, the elite Greek troops emerged and opened the city gates, whereupon the Greek army marched in and trashed the city.
CryptoLocker does its business in much the same manner, hiding itself primarily in emails as a .zip attachment from some official looking organization. Thus far these forged emails appear to come from organizations including financial software publisher Intuit, or from UPS, Federal Express, and DHL. The attached zip file contains an .exe, or executable, which when double clicked in its email host will unzip itself and run the executable. The executable takes just a few moments to install the virus on the new host computer, at which point the whole business disappears from the screen and goes off in the background to do its nasty work. Meanwhile, other than the brief blip on the screen, the user is completely unaware that the virus is busy encrypting every data file on the machine, rendering all files except .exe and system files into unusable jibberish.
A neat little trick, yes? Well, hold on because it gets worse.
According to the United States Computer Emergency Readiness Team, or US-CERT, a division of Homeland Security, CryptoLocker has the ability to find and encrypt files located on not just internal drives, but also shared network drives, USB drives, external hard drives, and even some mounted cloud storage drives. Should you have any mapped network drives on your computer, these can also become infected and encrypted. You can find the US-CERT alert page here: <http://www.us-cert.gov/ncas/alerts/TA13-309A>.
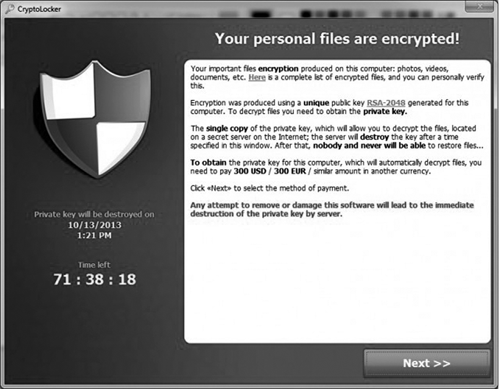
The files are encrypted using extremely strong algorithms (a 2048-bit version of the RSA cryptographic algorithm), making it virtually impossible to decrypt the files without the decryption key. During the encryption process an asymmetric pair of keys is created; one public, and one private. The public version of the key is left on the target computer, while the private key, which is the one actually necessary to decrypt the files, is sent off to one of the bad guys’ servers, which is of course well hidden. A lovely ransom note, crafted in broken English, then appears on the user’s screen, explaining that that private key will be destroyed in 72 hours if the user doesn’t cough up US$300 or €300 in either BitCoin or MoneyPak payment cards, both of which are digital currencies. The note further threatens that at the end of 72 hours, the private key on the bad guys’ server, will be destroyed.
THIS IS NOT A TOY
While this bit of computer malware is of course inherently evil, one has to marvel at its cleverness. Once infected, the computer and all of its attached files are essentially rendered useless. Unless a user is willing to pay, there is no known way at this time to recover the encrypted files. Should the user employ an antivirus or other malware mitigation program to destroy the CryptoLocker application, there will be no further infection, but of course the private key will ultimately be destroyed when the clock runs out.
This is not a fun little hack developed by some script-writing kiddie working in mom’s basement. This is a highly sophisticated piece of computer software technology. And it is lethal. The only way to protect oneself from CryptoLocker is to avoid infection in the first place. Of course, US-CERT recommends not paying the ransom, and instead reporting the incident to the FBI... which of course will not get your files back. You’re pretty much screwed there.
At this point, most users affected by CryptoLocker have chosen to pay the money, and have actually received the private key which decrypted their hard drives. Because law enforcement has been working to take down the bad guys’ servers where the private keys are located, and has done so with some success, some users who have paid the ransom have actually not been able to get their files back because the bad guys’ server had already been destroyed along with the private keys stored there.
WHAT TO DO?
The only surefire way to avoid losing files permanently is to have a recent backup of all files. Allow me to repeat that: the only surefire way to avoid losing files permanently is to have a recent backup of all files. Moreover, since CryptoLocker will find any external volume which is mapped to the computer with a letter (such as F:), the backup volume should be disconnected from the computer after a backup has been completed. If the backup volume is still connected, then it too will be encrypted.
This past week, a newer version of CryptoLocker has been seen in the field. The bad guys have actually added “features” to it, some which are sort of “beneficial”, and a few that are definitely not. Among the latter is a feature which destroys any shadow copies of the file system, if they exist on the hard drive. This feature will thereby make it impossible to either restore the encrypted files from the shadow copy, or to perform a system restore in Windows using a restore point. It will no longer work, because the necessary copies no longer exist. The “beneficial” feature, if you can call it that, provides an option that allows the user to pay the ransom at some time in the future greater than 72 hours from the original notice. So you could think about your predicament for several days, should you choose to do so. The bad news is that paying after 72 hours raises the price to 10 BitCoins. The price of a BitCoin at this writing is US$260, making that ransom option worth US$2600.
THIRD PARTY SOLUTIONS
Most of the major antivirus vendors have now included tools that will remove the CryptoLocker virus from your computer. Unfortunately, if your stuff is already been encrypted and you don’t have a backup, you’re still screwed since the AV programs don’t have the private key, nor do they have any way of cracking the encryption -- it’s just too tough.
There is one product that is just been released that actually appears to prevent infection in the first place. Please keep in mind that I have not personally tested this product, and cannot vouch for its effectiveness. However, several of the online sources that I follow and trust in the area of virus prevention and mitigation have recommended this product as a good one.
The product is called CryptoPrevent, and it runs on all versions of Windows from XP up to and including Windows 8.1. It was written by John Nicholas Shaw, whose website is Foolish IT dot com. Unfortunately, the site’s name yields a rather unsavory URL as follows: <http://www.foolishit.com/vb6-projects/cryptoprevent/>. At the bottom of the page you can find download links for the free version of the program. He also offers a premium version (the regular price is $25, but at this writing there is an introductory price of $15) which can be installed on multiple computers owned by a single user, and features automatic updating. These features are not included in the free version.
CryptoPrevent works by inserting specific group policy objects into the Windows registry. A group policy is a rule which prevents certain applications from running themselves, or certain users from running specific applications. Think of it as an internal firewall inside Windows that will disable the bad guys’ programs. It appears that CryptoPrevent will not disable any legitimate programs, although some users report trouble running Spotify after installing it. This problem exists primarily because of Spotify’s poor programming practices, but the author has implemented options that allow even poorly programmed applications that are known to be okay to be run despite the group policy rules.
DA FOUR RULES
Given the initial success of CryptoLocker -- Symantec estimated that one ransomware syndicate cleared in excess of $5 million in one year -- you can expect more of these Interwebz nasties to appear in the future. Nearly all of them rely on what is called social engineering, the practice of (often successfully) fooling a user into clicking on a link that takes them to a malicious website where a payload of badness is delivered on to their hard drive at once. The users thinks that they are protecting their bank account, or their PayPal account, or their Gmail account, when in reality they are getting a payload of exactly what they are trying to avoid.
The best way to prevent being infected in the first place, other than completely disconnecting your computer from the web (not a really good option), is to simply be careful. Here are four rules that will help you avoid becoming a victim of ransomware, identity theft, and other unpleasantness.
Rule #1 – Never Click an Email Link. This is the first rule for a reason -- it deals with the primary vector for online infection, which is a link in an email. More users get bit on the butt by clicking innocent-looking links in an email message than they do any other way. No matter how legitimate the email appears, no matter how legitimate the link appears, just do not click it. Email links can be forged and hidden -- the visible part of the link may be legitimate, but the actual link itself in the emails code may point you to somewhere completely different.
If you absolutely have to see where that link goes, you can manually type the visible link into the URL address box of your browser. Just understand that when you do even that, you are still taking a risk that can be avoided. Try contacting the sender instead by phone, and inquire as to the purpose of the link.
Rule #2 – Don’t Open Email Attachments. Email attachments are the second-most common vector for infection, and it is currently the most popular way to get infected with CryptoLocker. Again, the smartest thing to do is simply not click the attachment. Remember, email address fields can also be forged, so an email from someone you know may not come from that individual’s email account.
If someone I know since me an attachment of any kind, the first thing I do is call them on the phone and ask them if they intended to send me an attachment, and exactly what the attachment is, and why I need to see it. It’s also the case that many email programs will automatically display an attachment in a window. The act of displaying that attachment usually opens that attachment in the background, which is precisely where trying to avoid. If your email program automatically displays attachments, find the menu item to disable that function and set it to disabled.
Rule #3 – Backup Your Stuff. Regularly. I know, we’ve all been told that for years. It’s amazing how many people simply ignore this advice. Perform regular backups of everything. Put them on an external drive that can be removed, and after the backup is done remove it. Best practices for backup include keeping all digital data in three places: 1) on the computer’s hard drive where it was originally generated; 2) on an external backup drive; 3) on either an optical drive or on some form of cloud storage.
Computer users who really care about their data believed that that digital data does not really exist at all unless it exists in three different places, and on at least two different media formats.
Rule #4 – Keep Your OS Updated and Your Passwords Fresh. Those of us who run some version of Microsoft Windows know and follow Microsoft’s Patch Tuesday schedule. On the first Tuesday of every month, Microsoft releases updates to the various versions of Windows, and the diligent user will check to see what has changed and what security patches have been released. It’s not difficult, and it doesn’t take much time, but as long as Microsoft’s engineers have gone to the trouble of fixing their goofs, then we may as well take advantage of that.
Although it’s inconvenient, it is also a good idea to change your passwords on sites you visit regularly, and do that on a regular basis as well, and passwords need to be long. The longer the better. Remember, Adobe recently suffered an intrusion that resulted in the expropriation of somewhere in the neighborhood of 150 million usernames and passwords. Hey, it happens.
As the sergeant on NYPD Blue used to say, “Be careful out there.” Good advice.
♦

